Pioneering Device Security with Arm Security Architecture

In this growing digital age, the value of data has escalated, not just for legitimate uses but also among cyber criminals. The surge of connected devices and the Internet of Things (IoT) has amplified this issue, providing more and larger attack surfaces for hackers. Consequently, the race to secure devices has intensified, with the technology ecosystem striving to stay ahead of cyber threats.
For 30 years, Arm has pioneered security advancements. Our commitment to enhancing security practices and technologies is steadfast. We firmly believe that everyone in our ecosystem has a shared responsibility of prioritizing data security across their designas.
As the industry gathers for important events such as the Mobile World Congress, Embedded World, and the Game Developer Conference, data security is always an important topic of conversation. We’re also seeing various partners, such as ST Microelectronics, who have introduced their latest Arm-based security products in sync with these industry events. This offers an opportunity to reflect on the evolution of security within the Arm ecosystem.
At Arm, we’re dedicated to delivering a robust approach to security with our partners. We’re aware that we can’t do this alone, hence our active engagement with our ecosystem on architecture, IP, standards, certification programs, and open-source software. These innovative collaborations allow for the highest standards for data security across many products and devices.
What makes Arm’s security-focused architecture unique?
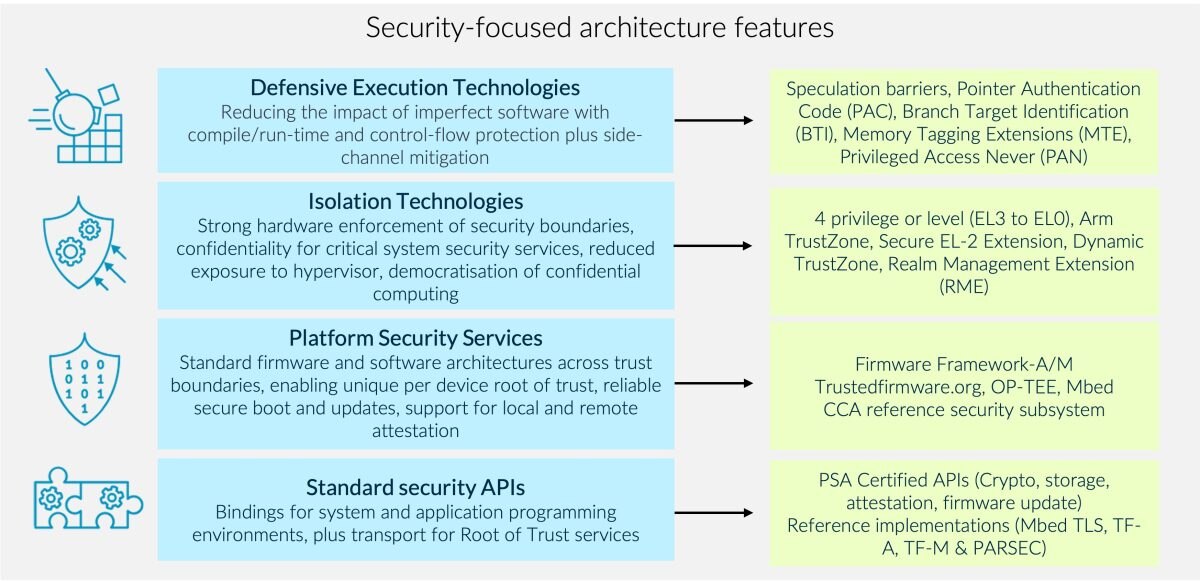
Our holistic approach to security begins with the fundamentals. Our architectures, including the A-profile, R-profile, and M-profile, are designed with inherent features that enable secure device construction from the ground up. We categorize Arm’s security features into four key areas:
- Defensive Execution Technologies
- Isolation Technologies
- Platform Security Services
- Standard Security APIs
Our latest ArmV9 architecture offers enhancements for building the trusted devices of the future. Considering Isolation Technologies, we’ve made significant advancements, including the introduction of Realm Management Extensions (RME). RME is an isolation architecture that allows hypervisors to create and manage a separate execution environment for workloads, distinct from both secure and non-secure worlds. We’ve also launched the Arm Confidential Compute Architecture (CCA), which builds upon RME to provide a reference firmware and software security architecture to support confidential computing requirements.
Armv9 also includes defensive execution technologies like the Memory Tagging Extension (MTE). This feature enables developers to identify and mitigate memory safety vulnerabilities before and after they deploy their applications on Arm-based mobile devices. MTE is already being adopted by Google across the Android stack, and device manufacturer Honor has made MTE-enabled MagicOS 6.x. and MagicOS 7 devices available to developers through Honor SkyNet. Kuaishou, a leading video-sharing platform with over 630 million monthly average users, also integrated MTE into its development cycles.
Many features we deploy in A-profile have equivalents in the M-profile architecture. For example, Arm TrustZone technology, which has been around for over 20 years, offers an efficient, system-wide approach to security with hardware-enforced isolation built into the CPU. It was initially launched in the A-profile and is now used in our Armv8-M family of processors. Defensive execution technologies like Pointer Authentication (PAC) and Branch Target Instructions (BTI) are designed to counter Returned-Oriented Programming (ROP) and Jump-Oriented Programming (JOP) attacks.
These are just a few examples of Arm’s commitment to security-focused architectures. We continuously maintain and update security features, with annual updates to the Arm architecture. These features are deployed into our product and solution roadmap, including Arm’s Total Solutions for IoT and Total Compute Solutions.
These are just a few examples of Arm’s investment into architecture features, part of our track record of delivering security features throughout the A, M, and R profiles. We also continuously maintain and update security features, with annual updates to the Arm architecture. These features get deployed into our products and solutions roadmap, including Arm’s Total Solutions for IoT and Total Compute Solutions.
Our open-source software team collaborates with hundreds of ecosystem partners, including TrustedFirmware.org, to deliver projects and specifications such as TF-A, TF-M, Firmware Framework, and PARSEC. This provides developers with quick and easy access to security software and services. We have also released the new PSA Certified firmware update API, a crucial component in addressing the challenge of keeping IoT devices secure and up-to-date throughout their lifecycle.
Dedicated security IP complements these robust foundations to enhance security further. The leading provider of secure silicon IP solutions Rambus will offer licenses for the Arm CryptoCell and CryptoIsland security IP portfolio. This collaboration improves accessibility to products that have been widely adopted by the ecosystem, with CryptoCell alone having over 100 licenses worldwide.
Leading the way in ecosystem collaboration for security
To make significant progress on security, we have to collaborate as an ecosystem to ensure scalability between markets and use cases. It’s not just something that Arm believes; the PSA Certified 2022 Security Report found that 96 percent of respondents want security guidelines from the industry. This nature of collaboration means that Arm is at the forefront of continued security research and collaborative programs with industry and governments.
Take for example, PSA Certified, the global security certification scheme for IoT devices, which Arm spearheaded in partnership with leading security testing labs in 2019. It provides a security framework for manufacturers to create secure, trustworthy IoT devices that comply with industry security best practices. Manufacturers can work with a PSA Certified independent evaluation lab to assess the security of devices at three different levels of assurance. The certification program helps to build trust in IoT devices and provides a common standard for the industry to follow, which helps to reduce the fragmentation and complexity of the IoT security landscape.
While this is just one example of our work in this space, it’s a powerful one: with nearly 150 Arm-based products from almost 80 companies PSA Certified to date.
Another more recent example of an Arm-led security collaboration is the Arm Morello program. Morello is a joint effort between Arm, the U.K. Industrial Strategy Challenge Fund Digital Security by Design, and several leading UK universities, including the University of Cambridge, the University of Edinburgh, and the University of Manchester. Rather than looking at security best practices, this program is focused on developing a new type of processor architecture – Morello – which is designed to provide enhanced security features at the hardware level.

Morello extends the Arm architecture with unique features that can help mitigate memory safety vulnerabilities, such as buffer overflows, which are a common target for cyber-attacks. The program is part of a broader effort to create a more secure computing infrastructure, which is becoming increasingly important in the face of growing cyber threats.
Over a year has passed since the Morello program celebrated the first availability of prototype system-on-chips (SoCs) in January 2022. Over 500 Morello boards have now been distributed to our ecosystem of security specialists, software companies, tools developers, and leading academic institutions who are testing, writing code, and collaboratively providing critical feedback to identify whether Morello is a viable security architecture for the future.
Trusted future of computing built on Arm
Securing the world’s data will be a significant challenge in the next decade, requiring robust collaboration within the industry. Arm is heavily investing in new architectural features for more secure solutions and in standards and research initiatives to drive industry progress.
While cybercriminals could be formidable adversaries, the scale and dedication of the industry and its brightest, most visionary security minds can make the hackers’ jobs increasingly difficult.
Arm is your trusted partner in this endeavor. Together, we can make the digital world a safer place.
Security built on Arm
Arm and our trusted ecosystem enable secure experiences wherever computing happens.
Any re-use permitted for informational and non-commercial or personal use only.












